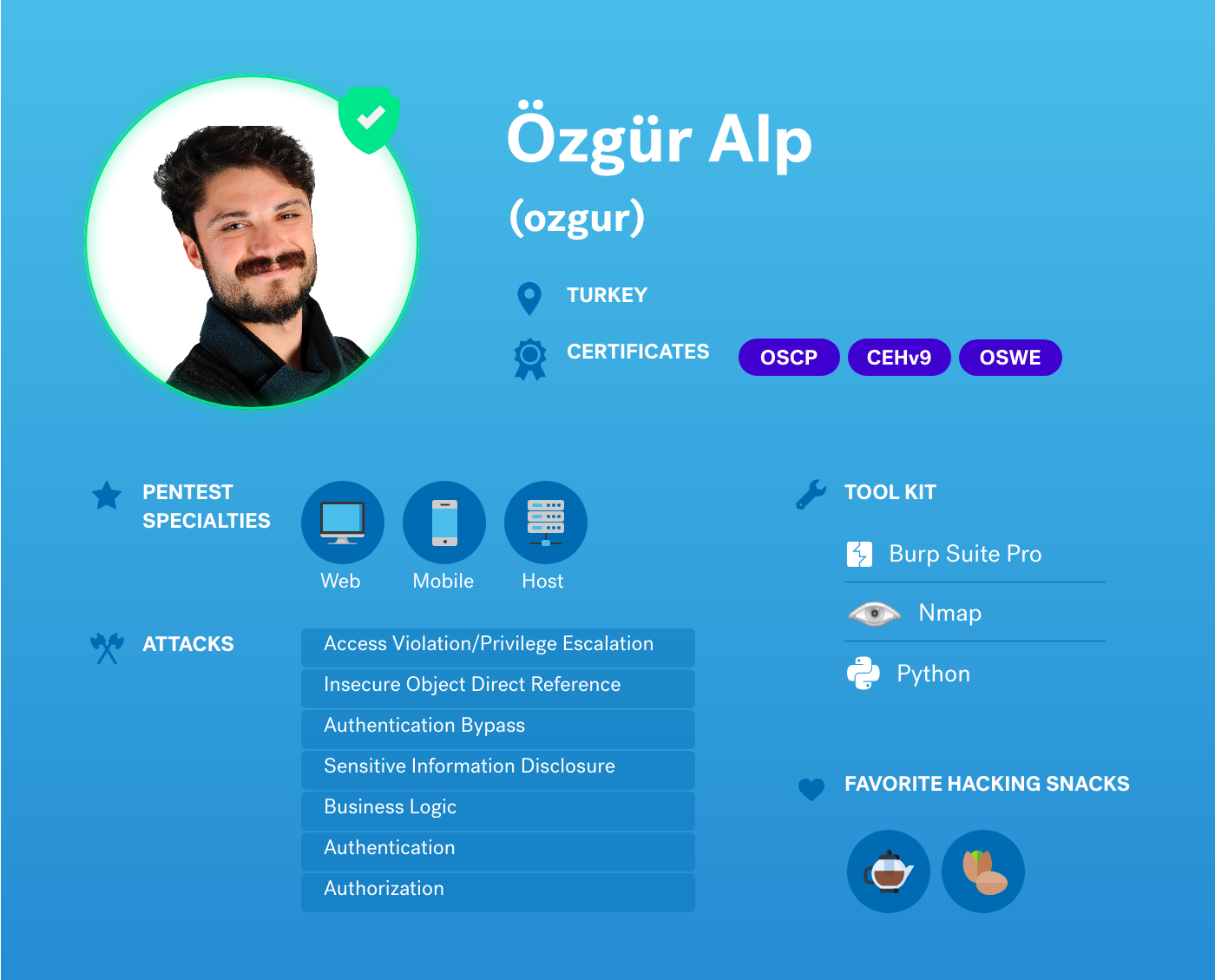
Özgür Alp is an offensive cybersecurity specialist, lecturer, and instructor with over 7 years of experience as both a pentester and bug hunter. He has been involved in over 500 on-field and remote security programs with multinational companies across various industries. Over the past 3 years, he has been lecturing on topics around web and mobile application security at two reputable universities in Istanbul, Turkey.
Özgür joined the Cobalt Core, our highly-experienced, geographically-diverse community of pentesters, in February 2019. He is one of the 250+ pentesters worldwide who has helped Cobalt secure over 2000 applications to date. We had a chance to hear from him to learn more about his pentester origin story and what he enjoys about being a part of Cobalt’s pentest community.
We had a chance to hear from him to learn more about his pentester origin story and what he enjoys about being a part of Cobalt’s pentest community.
Pentester Origin Story: How did you get into security?
OA: I’m not one of those “wonder kid hackers” who started by hacking large technology companies at age 10. My interest in cybersecurity began during the last year of my Bachelor studies where I was pursuing a degree in Information System Engineering. That being said, as a child, I had always been interested in puzzles, challenges, and brain teasers. There was something about putting puzzle pieces (both physical and mental pieces) together in a logical way in order to arrive at an intended solution. The challenge, and one’s ability to overcome these obstacles, has always been a passion of mine. I still consider puzzles to be one of my favorite hobbies, and believe that it has contributed to my interest and success in finding security vulnerabilities.
My career in offensive security started when one of my university professors gave a small assignment on Hackquest, a hacking challenge where the goal is to solve challenges related to information security including tasks around reverse engineering, web, mobile hacking, and pentesting. For me, it was like the ultimate puzzle, and ended up being the first offensive security challenge I successfully solved.
During an interview after graduation, I met my first security mentor, and later to become my manager, Burc Yildirim. After our very first meeting, I told myself that I wanted to start my career working with him and since then he has been a role model of mine. Burc inspired my career from a technical approach, pentest methodology, and business strategy. As my manager he helped me quickly adapt my love of challenges and puzzles into a successful career in the wild west private sector.
What motivates you when it comes to pentesting?
OA: Conceptually, offensive security is very similar to my favorite hobby: solving puzzles. I enjoy the act of solving complex problems and chasing that “Aha!” moment. The feeling of finding a critical vulnerability after hours of research is truly incomparable. Pentesting brings an always evolving challenge which keeps me motivated and helps me continuously improve upon my technical skills. The biggest motivator for me is simply doing what I love to do, competing with the best out there, and getting paid for it.
What does a good pentest engagement look like?
OA: The more information a pentester has about the systems that he/she is testing, the more successful the outcome. From a pentesters perspective I can say that a good pentest should always includes these steps:
- Gather information about the target and get to know the application or system.
- Asks questions to both business analysts and developers of the applications.
- Share potential weaknesses discovered that cannot be exploited further and assess them with the application/system developers.
- Grant access to the source code for pentesters. White-box pentesting always wins.
What are the top 3 traits that a pentester should possess to be successful on Cobalt?
OA:
Analytic Intelligence: The ability to understand technical concepts behind the technologies being pentested and an amplitude for deep understanding of these technical concepts. Detail Oriented: Attention to detail is beneficial as a pentester because vulnerabilities are most often not visible in plan sites. They are hidden in the details and as a pentester you must find them.
Customer Relations: Effective communication skills to effectively communicate issues to customers. Also telling the vulnerability correctly is important as finding the vulnerability as well for a quick remediation.
How do you organize yourself during a pentest?
OA: Organization is key, especially when you are working on a time-boxed pentest project. It’s important to divide your “To-do list” by specific days and hours. I find that the more I am able to split up my tasks the easier it is to manage myself and expectations. Each day I go through what I have covered, what I still need to cover, and I like to predict what I expect to accomplish the following day. Personally, I like to break it down by week, day, and hour.
Due to the nature of this job, some exploitations can take longer than first expected. Because of this it’s always beneficial to add an hour or 2 buffer. For example, if you block off 8 hours of tasks, you should budget, at least, another hour or so in case you go over (it always does). This will make sure that you stay on track for your other tasks
What kind of targets excite you the most?
OA: I’m all about the challenge, so the more complex and hardened the target the better! I especially like the ones with unique business logic structures that challenge my technical skills and allow me to think about it from a more practical use case point of view.
What do you enjoy the most about being a part of the Cobalt Core?
OA: Being a part of the Cobalt Core has connected me to like-minded offensive security experts from around the world. It has been amazing to share both technical experiences and the feelings that come with working in the offensive security arena. Working with folks from Argentina to New Zealand brings a more holistic and worldly vision to how I approach security.
Do you have a favorite vulnerability type?
OA: My favorite vulnerability type is authentication bypasses, especially for the ones which are designed for administrators. I always love to access functionalities of the administrators on unauthenticated tests.
What has been your favorite moments as a Pentester on the Cobalt Core?
OA: Recently, I was involved in a pro-bono project for a Health Tech company developing applications to aid during the COVID-19 pandemic. With the current state of the world, many people are trying to help in whatever ways possible. As an offensive security researcher, it’s no different. For me security is a passion and I am happy to use and share my knowledge to help organizations that are doing their part to aid during these tough times. While I see this as a small act, I am happy to be able to offer my assistance and contribute during times of need.
What made you want to be a part of a program like this?
OA: People around the globe are contributing to the community and doing their best to overcome the challenges of the pandemic, it feels good to be able to use my skills to be a part of the contributions.
How has pentesting changed or do you approach pentesting differently in the age of COVID? Do you have any advice for organization during these times?
OA: Pentesting conditions haven’t changed too much; however, demand for offensive security has increased. Many bad actors see times of chaos, such as a global pandemic, as an easier opportunity to attack organizations and cause even more distraction.
When it comes to pentesting, a tester should always access the application or system by taking in external information. We need to assess it considering many different aspects. It is especially important to be doing that in the age of COVID. In these times denial of service related vulnerabilities are quite important and impactful due to the increases in potential disruptions.
If you haven’t pentested your systems before, now it is the time before it would be too late. If your business continuity is important for the society in this time of the pandemic, please make sure your systems are solid to avoid denial of service attacks to avoid disruptions & potential chaos moments.
You can take a look at other Core pentester profiles. Interested in joining the Cobalt Core? Apply here.














.png)


