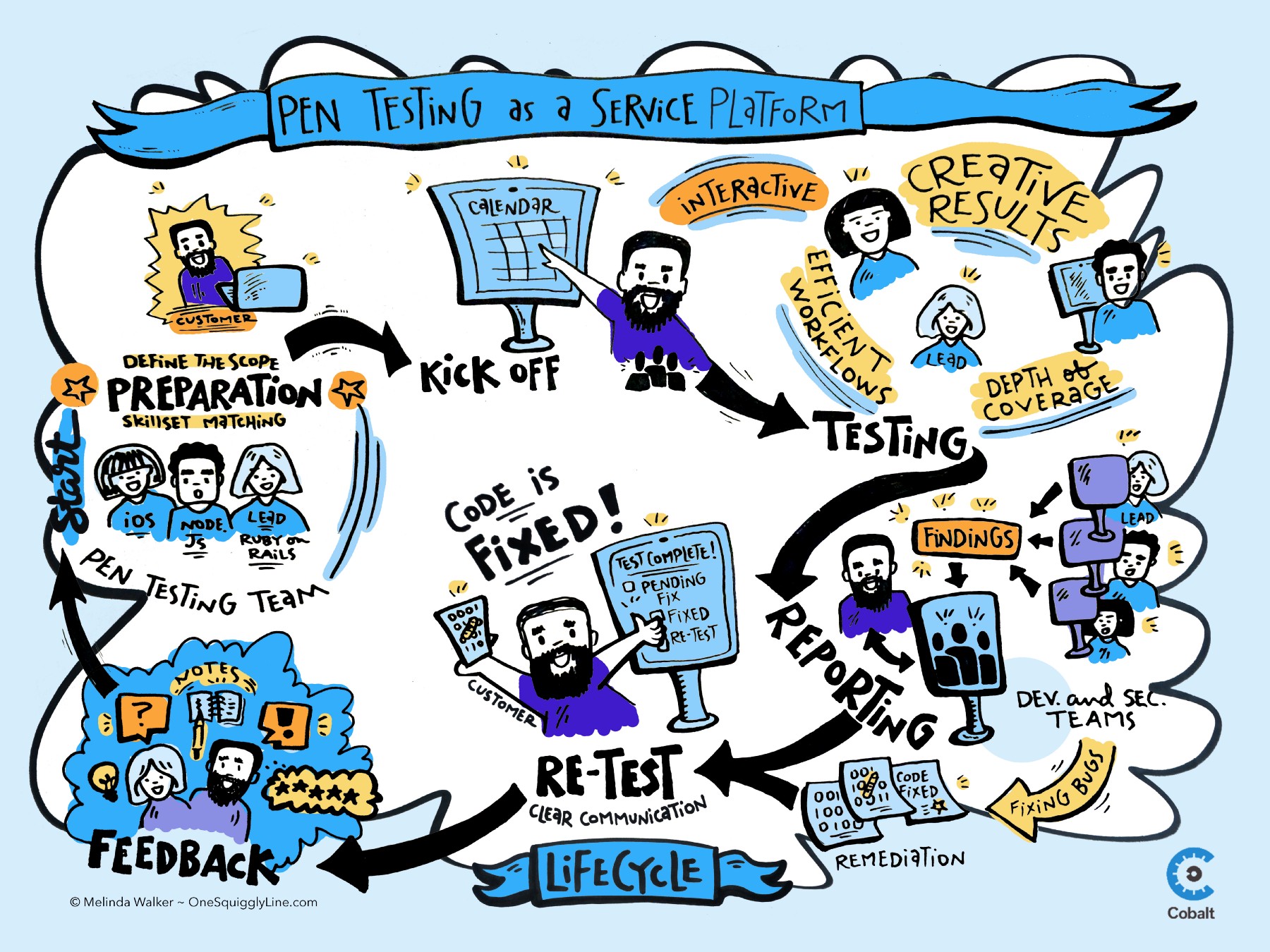
The Pentest as a Service model combines data, technology, and talent to resolve security challenges for modern web applications, mobile applications, and APIs. This new approach applies a SaaS security platform to pentesting in order to enhance workflow efficiencies.
Key roles in this new process include:-
Customer: Security and engineering teams using Cobalt services
-
Cobalt PenOps Team: Schedules, manages, and facilitates the pentest process
-
Cobalt Core Lead: Facilitates conversation between Pentest Team and Customer
-
Cobalt Core Domain Experts: Leverage specialized skill sets which are matched to the Customer’s technology stack
-
Cobalt Customer Success Team: Works closely with the customer to kick-off the test and address feedback
All 6 phases of Pentest as a Service, as visualized in the infographic above, happen in the cloud on the Cobalt platform and Slack channel.

Phase 1. Preparation
The first step in the Pentest as a Service process is to prepare all the parties involved in the engagement. On the Customer side, this involves determining and defining the scope of the test and creating accounts on the Cobalt platform. The Cobalt PenOps Team assigns a Cobalt Core Lead and Domain Experts with skills that match the Customer’s technology stack. A Slack channel is also created to simplify on-demand communication between the Customer and the Pentest Team.
For more information about the Preparation phase, check out 3 Tips for Preparing for a Penest.

Phase 2. Kick Off
The second step is kicking off the pentest. This will typically involve a 30-minute phone call with the Customer and Cobalt Teams. The main purpose of the call is to offer a personal introduction, align on the timeline, and finalize the testing scope.
For more information about this phase, check out 4 Tips to Successfully Kick Off a Pentest.

Phase 3. Testing
The third step is where the pentesting will take place. Steps 1 and 2 are necessary to establish a clear scope, identify the target environment, and set up credentials for the test. Now is the time for the experts to analyze the target for vulnerabilities and security flaws that might be exploited if not properly mitigated.
As the Pentest Team conducts testing, the Cobalt Core Lead ensures depth of coverage and communicates with the Customer as needed via the platform and Slack channel. This is also where the true creative power of the Cobalt Core Domain Experts comes into play.
For more information about this phase, check out 6 Pentest Phases: An Inside Look at Pentesting .

Phase 4. Reporting
The fourth step is the reporting phase, which is an interactive and on-going process. Individual findings are posted in the platform as they are discovered, and at the end of a test the Cobalt Core Lead reviews all the findings and produces a final summary report. Once the report is complete, it is sent to the customer.
The report is not static; it’s a living document that is updated as changes are made (see Re-Testing in Phase 5).
For more information about this phase, check out 4 Tips for Making the Most of a Pentest Report.

Phase 5. Re-Testing
It’s important to identify vulnerabilities in your applications, but most important is fixing the issues that are found in order to improve the security and quality of the code. Once the Customer is aware of the security issues identified during the pentest, addressing each issue happens over the course of the next few weeks and months. When the Customer marks a finding as “Ready for Re-test” on the platform, the Cobalt Core Lead verifies the fix and the final report is updated.
For more information about this phase, check out Best Practices for Verifying Vuln Fixes.

Phase 6. Feedback
Once the testing is complete, the report has been sent to the Customer, and remediation is in the works, Cobalt’s Customer Success Team reaches out to the Customer for feedback. Customers initially provide feedback through a five-question survey which allows them to rate the overall process, findings, and full report.
During a scheduled feedback call, Customers dive deeper into their survey responses as needed and align with the Cobalt Customer Success Team on action items and expectations moving forward. This feedback helps the Cobalt team to continue to improve the process for upcoming tests and shape the platform product roadmap moving forward.
For more information about this phase, check out 3 Key Factors for Improving a Pentest.
Concluding Remarks
Without applying a lifecycle approach to a Pentest Program, an organization is doomed to treating security as a point-in-time project rather than a continuous function. By its nature, a project has a start and end date. When the project is complete, everyone moves onto the next thing.
It’s important to treat a Pentest Program as an ongoing process. Step 6, the Feedback Phase, should always lead into the preparation for the next pentest whether it’s happening the following week, month, quarter, or year.
Sign up here for a demo of Cobalt’s Pentest as a Service platform.